Get ISO 27001 certification ready - without starting from scratch.
Fast Track ISMS, built from 26 years’ experience, gives SMEs the templates, structure, and optional expert support to build an Information Security Management System (ISMS) that meets ISO 27001 requirements and stands up to audit.
A simple plan.
Step #1
Create a certification plan.
Fast Track ISMS provides the starting blocks to create a plan to get you to certification with key milestones.
Step #2
Build the foundations for an Information Security Management System (ISMS) that meets your business needs and stakeholder expectations.
Step #3
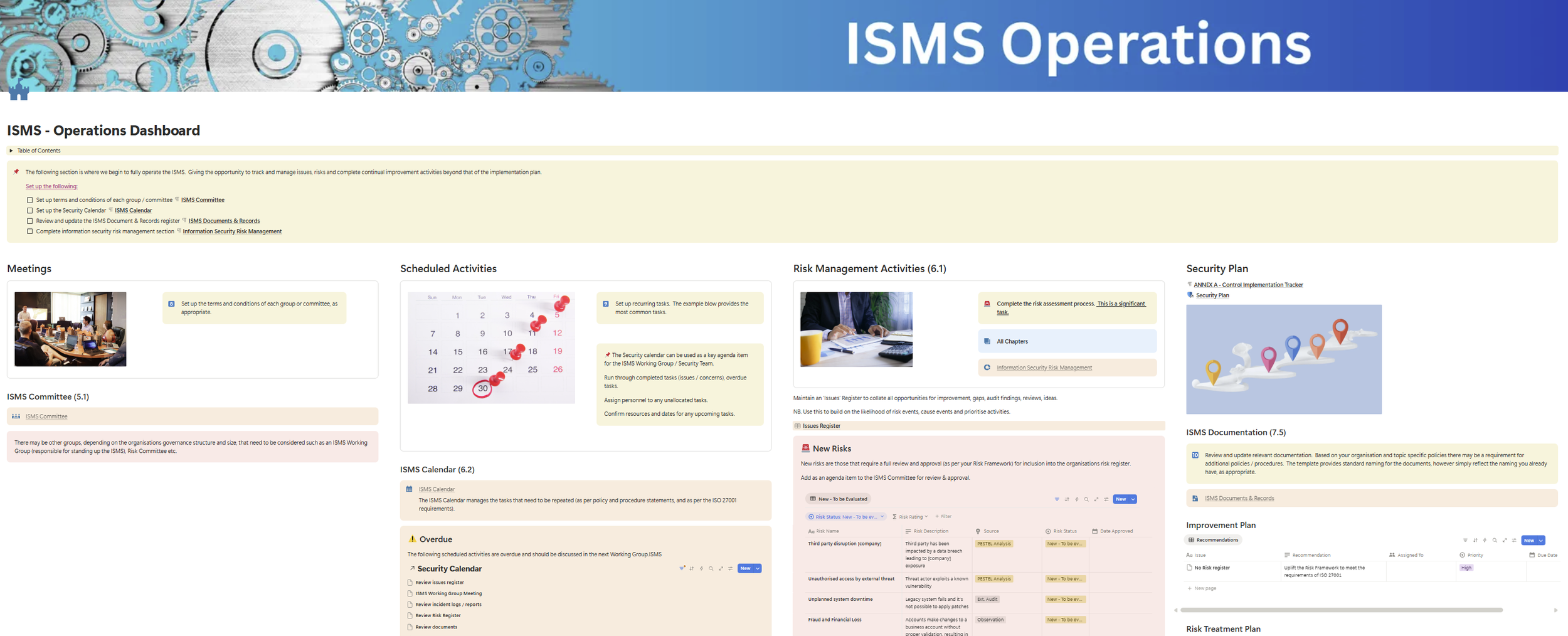
Operate your ISMS through a high level dashboard that keeps you ahead of the tasks, risks and day to day operations required for good security and business resilience.
We fully understand the data sovereignty expectations of some clients and have therefore summarised how the Notion solution can integrate with O365 and ServiceNow - commonly used to maintain more sensitive artefacts such as the Risk Register. Read more below:
Client Testimonial
Wondering what it’s like to work with Elev8 Resilience?
In this quick video, Tiimely and FOUR share their experience of partnering with us – how we helped them to make sense of ISO 27001, build on the work they’d already done, and cutting through the jargon to giving their teams confidence in the process and the outcome.
About Us
Elev8 Resilience was founded on the principle of collaboration and the integration of specialist disciplines to provide comprehensive and effective services.
Our founder recognised the immense benefits of bringing together diverse expertise and has built Elev8 Resilience to connect the best minds and experiences in the industry.
At Elev8 Resilience, we value diversity of thought, drawing from personal experiences, cultural backgrounds, and core business resilience disciplines. We believe in the power of combining business continuity, information security, privacy, data protection and cybersecurity to create robust solutions for our clients.
By engaging with key partners and industry thought leaders, we aim to foster a cooperative environment where resources are maximised, and innovation thrives. Our mission is to work together to achieve outstanding business outcomes in today’s fast-paced and ever-evolving world.
Our mission:
To help organisations innovate, optimise and succeed.
At Elev8 Resilience, our mission is to empower growing organisations to thrive amid uncertainty.
We help businesses transform compliance, cybersecurity, and continuity from barriers into enablers, giving them the confidence to scale, compete, and expand securely.
With decades of experience across government, finance, health, and critical infrastructure, we partner with organisations ready to take the next step, guiding them to strengthen governance, meet new regulatory demands, and build the resilience needed for global opportunity.
We believe resilience isn’t built by chance — it’s designed.
About the Founder
Founder / CEO
Yvonne Sears
A dedicated subject matter expert with over 25 years’ experience in information security, business continuity, cybersecurity, privacy consulting and advisory services across the UK and Australia.
She has worked with multiple complex industries from Critical Infrastructure, Banking and Government to small specialist companies servicing Defence through innovative technology solutions.
With the multi-disciplined approach and vast experience Yvonne can design strategies that are aligned to the business needs and stakeholder expectations. By providing a prioritised roadmap based on risk, she ensure robust and effective business resilience solutions.
Yvonne is well regarded within the industry and has served on the boards of ISACA, IAPP and BCI; is a Fellow in Information Privacy, an AISA Fellow and currently on the Standards Australia Committee providing subject matter expertise and input into revisions of various international and Australian standards.
-
Australian Institute of Company Directors (MAICD)
MSc Information Security & Computer Crime
LLM Information Law (Data Protection, FOI, Copyright)
Fellow of AISA (FAISA)
Fellow in Information Privacy (FIP) - IAPP
Certified Information Security Manager (CISM)
Certified Data Privacy Solutions Engineer (CDPSE)
ISO 27001 Master (Lead Implementer, Lead Auditor)
-
BCI Business Continuity and Resilience Consultant of the Year (2018)
BCI Business Continuity and Resilience Consultant of the Year (2020)
Nominated Global Award BCI Business Continuity and Resilience Consultant of the Year (2020)
2022 Nominated Information Security Women of the Year
2023 Nominated Protective Security Women of the Year
Industry speaker
Security Magazine Publications
-
Australian Standards Committee (ISO 27001:2022, ISO 27002:2022)
ISACA Privacy Book "Implementing a Privacy Protection Program" (2017)
Women in the Security Profession, Book (2016)
“Yvonne brings a unique perspective and approach to the information security and continuity industries at a time when it’s most needed. Her strong background in operational risk, business continuity and privacy strongly complement and enhance her information security approach.”
CISO, Mining
Our Partners
Through strategic partnerships with other companies and independent specialists, we have unlocked a world of opportunities that enhance our capacity to grow and broaden our skillset as and when it is needed.
These partnerships allow us to tap into specialised knowledge, access cutting-edge technology, and scale our operations with agility and efficiency.
Together with our partners, we form a formidable team, united in our commitment to delivering excellence and driving results.
Governance, Risk & Compliance
Technical and Cyber Threat Intelligence